Zcash is one of the privacy-focused cryptocurrencies along with other established peers such as Monero, and Dash. In today’s guide we will discuss what is Zcash as well as all the technologies that power it.
Zcash is a decentralized peer-to-peer cryptocurrency which was created as a Bitcoin fork. Just like Bitcoin, it has a total limit of 21 million coins. Nevertheless, these are all the similarities of Bitcoin and Zcash. The decentralized coin provides total privacy by using some of the most advanced cryptographic technologies.
What is Zcash?
Zcash was born on October 28, 2016, as a Bitcoin fork. Originally, it was named the Zerocoin protocol before it was converted to the Zerocash system and then it finally became Zcash.
Zcash was developed by the Zerocoin Electric Coin Company, also known as the Zcash Company. The company’s founder and CEO is Zooko Wilcox.
How does Zcash work?
The easiest way to understand Zcash transactions is to see how they are different from Bitcoin transaction.
If Dave wants to send Carol 1 BTC the amount will be sent to Carol’s public address. The miners add the transaction data within their blocks to complete it.
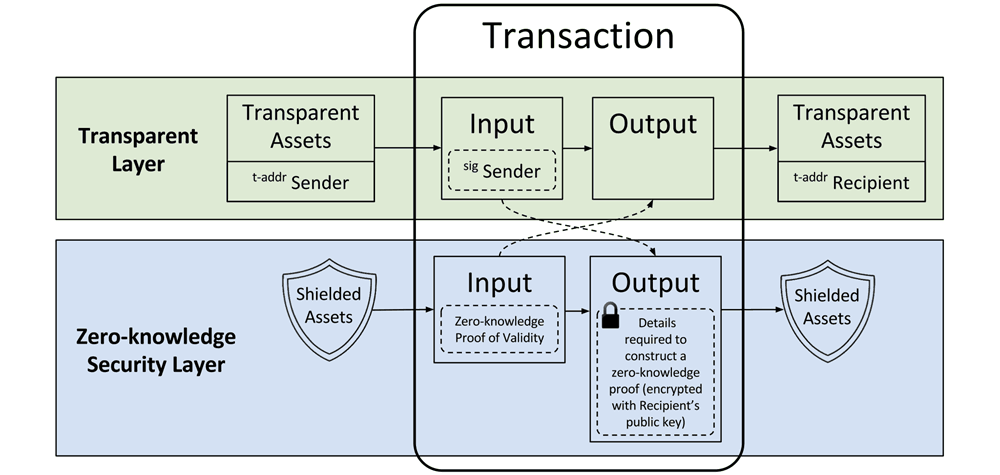
When performing a Zcash transaction there are in fact two types to choose from. You can select the regular transparent transaction or use the shielded private transaction.
Let’s say Dave wants to send 1 ZEC to Carol. If Carol decided to keep the transaction transparent (so everyone can see the details) then Dave can send her the ZEC to her transparent address (t-addr).
If Carol wants a private transaction instead, then Dave can send her the amount to her shielded address (z-addr).
Should both parties use their shielded addresses when performing the transaction than it would be completely private. All transaction details would be inaccessible to everyone else including Dave and Carol’s identities, as well as the transaction data itself.
Zcash’s full transaction privacy is achieved by using zk-SNARKS or Zero-Knowledge Succinct Non-Interactive Arguments of Knowledge. We will discuss this method in detail below.
What are zero-knowledge proofs?
Zero-Knowledge proofs were developed in the 80’s by MIT researchers Shafi Goldwasser, Silvio Micali, and Charles Rackoff.
They were trying to solve problems linked to interactive proof systems, in which a Prover communicates with a Verifier to persuade them that they have knowledge of a certain proof without detailing that knowledge.
Before their discovery, the majority of proof systems were based on “soundness” properties. It was a common assumption that the Prover could be the malicious one in any case example in which they attempt to trick the Verifier. The 3 MIT researchers questioned the morality of the Verifier instead of the Prover. The problem was, how can someone know for sure that the Verifier won’t leak the knowledge. Another issue was how much knowledge about the Prover will the Verifier find out during the verification process.
In the real world, this puzzle has various consequences and one of the most well-known is related to password protection.
If you were to login to a website with a password the common protocol is that you, the client, will fill in their password which will be sent to the server. Then, the server will hash the password and see if it matches with the hash thei have stored in their system. If the values are the same, you are allowed to enter the system.
As you can see, this system is deeply flawed security-wise. The server (Verifier) has your password stored in plain text version and your privacy depends on it. Should the server become compromised in any way, your password could be accessed by an unauthorized third-party.
Zero-knowledge proofs were created to counter such scenarios. There are two parties involved (the prover and the verifier) in a zero-knowledge proof (ZKP). Zero knowledge states that a prover can prove to the verifier that they have a certain knowledge without telling them what that knowledge is.
Properties of a zero-knowledge proof
To work, a Zero Knowledge Proof needs to have a specific set of parameters:
For a ZKP to work it needs to satisfy certain parameters:
- Completeness: If the statement is true, an honest verifier can be convinced of it by an honest prover.
- Soundness: If the prover is dishonest, they can’t convince the verifier of the statement’s soundness by lying.
- Zero-Knowledge: If the statement is true, the verifier won’t find out what the statement actually is.
Let’s see one of the most popular zero-knowledge proof example, called Alibaba’s Cave.
In this example, the prover is saying to the verifier that they know the password of the secret door at the back of the cave and they want to prove it to the verifier without revealing the password itself.
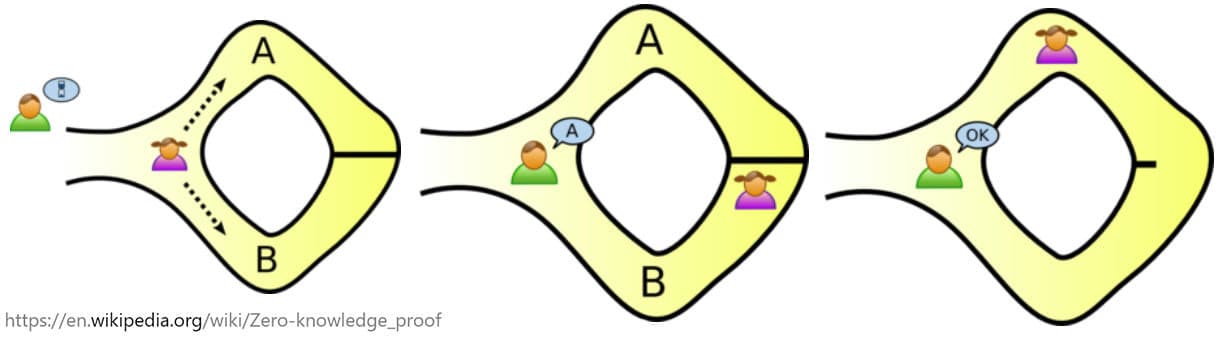
The prover (P) will take both paths A and B. Let’s say they take path A first and get to the secret door at the back. Then, the verifier (V) comes in at the entrance without knowing which path the prover took and states they want to see the prover appear from path B.
The diagram above illustrates the process. But what if this was just a lucky situation? What if the prover didn’t actually know the passcode, took the path B and they were stuck at the door. Then, by luck, the verifier told them to return via path B, which they were already on.
To test the validity, the experiment is performed multiple times and the prover needs to show up at the correct path every single time. This way it will prove to the verifier that they know the password even if the verifier doesn’t know the actual password.
Like for any other case, Alibaba’s Cave needs to satisfy the main ZKP properties:
- Completeness – The statement was true so the honest prover convinced the honest verifier
- Soundness – If the prover was dishonest, they couldn’t have tricked the verifier since the test was repeated multiple times to eliminate the luck factor.
- Zero-Knowledge – The verifier never found out the password but was convinced that the prover possesses it.
Non-interactive zero-knowledge proofs
The initial zero-knowledge verification systems had a major problem. For such a system to work, both prover and verifier had to be online simultaneously which made the process “interactive”. This made the system inefficient and extremely difficult to scale up.
Fiat and Shamir invented the Fiat-Shamir heuristic back in 1986 and turned the interactive zero-knowledge proof to non-interactive zero-knowledge prof allowing the new protocol to work without any interaction.
To see the difference, let’s start by looking at how zero-knowledge proof used to work before the Fiat-Shamir heuristic using simple discrete logarithms.
Carol wants to prove to Dave that she has knowledge of a value x such that y = g^x to a base g.
Carol select a random value v from a set of values Z and computes t = g^v and sends t to Dave.
Dave chooses a random value c from the set Z and sends it to Carol.
Carol computes r = v-c*x and returns r to Dave.
Then, Dave checks if t= g^r * y^c holds or not ( since r= v-c*x, y= g^x and by simple substitution, g^(v-c*x)* g ^ c*x = g^v = t).
While Dave doesn’t know the value of x, he can check if t = g^r * y^c to verify that Anna does know the value of x.
The interaction above is zero-knowledge but the problem is both Carol and Dave need to be online and exchanging values which makes the process “interactive”.
The Fiat-Shamir heuristic solve the problem by using a simple cryptographic hash function. Here’s how the example above would work as a non-interactive zero-knowledge proof:
Carol wants to prove to Dave that she knows a value x such that y = g^x to a base g.
Carol selects a random value v from a set of values Z, and computes t = g^v.
Carol computes c = H(g,y,t) where H() is a hash function.
Carol computes r = v – c*x.
Then, Dave or anyone else can check if t = g^r * y^c.
Now that we discussed how zero-knowledge proofs became non-interactive, let’s discuss Zk-Snarks which rely on them.
How are Zk-Snarks being used?
As I already mentioned, Zk-Snarks stands for “Zero-Knowledge Succinct Non-Interactive Argument of Knowledge”. Their use in current blockchain technology is incredibly important but to understand it, you also need to understand smart contracts.
Smart contracts are scripts that automatically execute when a preset collection of conditions is met. If you’re interested in learning more about smart contracts please check our in-depth Ethereum guide.
For example, Carol places 100 ETH in a smart contract that she enters along with Dave. Dave needs to perform a specific task and once completed he will receive the 100 ETH from the smart contract.
Obviously, things aren’t always so simple so Dave might have to perform several multi-layered and confidenial tasks. What if Dave would need to perform tasks A, B, and C to receive the payment but you don’t want to reveal the details of these tasks since they are confidential to your business and competitors shouldn’t find out about them?
Zk-Snarks is able to prove that the tasks have been completed in the smart contract without revealing details about them. It is a powerful tool in maintaining privacy for both businesses and individuals. It can simply reveal part of the process without exposing the entire process and prove that your claims are valid.
How do Zk-Snarks work?
A Zk-Snark comprises three algorithms: G, P, and V.
G is a key generator that takes an input “lambda” which remains confidential at all times and a program C. It generates two publicly available keys, vk, a verification key, and pk, a proving key. Both keys are public and accessible to any of the involved parties.
P is the prover that will use three items as input. The proving key pk, the publicly available random input X, and the private statement (we’re going to call it “w”) whose knowledge needs to be proved without revealing itself. The P algorithm will generate a proof prf such that:
prf = P (pk, x, w).
V is the verifier algorithm that returns a boolean variable. A Boolean variable can only have a TRUE or a FALSE value. The verifier algorithm uses the verifying key vk, public input x, and proof prf such as:
V(vk,x,prf)
If the prover is correct, the algorithm will return TRUE and FALSE otherwise.
The lambda parameter needs to remain confidential since it can be used by anyone to generate fake proofs. The fake proofs will return a TRUE value even if the prover doesn’t have knowledge of private statement “w”.
How is Zcash mined?
The algorithm used for block mining in Zcash is called equihash. It’s a Proof-of-Work algorithm based on the Generalized Birthday Problem that was created by Alex Biryukov and Dmitry Khovratovich.
The equihash algorithm is being used to make Zcash mining ASIC-unfriendly. Cryptocurrencies such as Bitcoin can be mined using specialized hardware called ASICs. The mining pools monopolize the mining of these currencies by investing heavily in ASICs to increase their mining efficiency.
Zcash has made its mining ASIC unfriendly to ensure the mining is as decentralized and democratic as possible.
You might be wondering what’s the deal with the Generalized Birthday Problem also known as the birthday paradox.
If you met a random stranger the chances that both of you have the same birthday are extremely low. Assuming that all days of the year have the same chance of having a birthday, the chances of another individual having the same birthday as you is 1/365, which is 0.27%.
Nevertheless, if you take a group of 20-30 people, the odds of two individuals sharing the same birthday are as high as 50%. This happens because of a simple rule in probability. If you have N different possibilities of an event happening then you need swuare root of N random items for them to have a 50% chance of a collision.
As a result, if you apply the same theory for birthdays there will be 365 different birthday possibilities. You simply need sqrt(365) which equals ~23 randomly selected people to have a 50% chance that two of them share their birthday.
If you’re considering the idea of mining Zcash yourself, we recommend you check our in-depth guide: How to mine Zcash.
Zcash coin distribution
Zcash is a Bitcoin fork, so the two currencies have some similarities. Just like Bitcoin, Zcash has a maximum supply of 21 million coins expected to be mined by 2032. The block reward gets halved every four years to regulate the supply.
It’s also worth mentioning Zcash is not ICO funded and there was no pre-mining period either. Instead, the coin had $1 million in funding from a group of closed investors for its initial development. The investors were promised with a 10% reward of the total supply in an incremental manner over the next 4 years. This reward is known as the “Founder’s Reward”.
Zcash regulation
Because of all the extra security measures, Zcash regulation is difficult but not impossible. Law enforcement can check the regulation using two methods: View Key, and Memos.
Each Zcash user has their own View Key. They can share it with someone else if needed. The View Key reveals all hidden transactions and allows anyone to see the owner’s transactions as well as the recipient’s address.
Zcash transactions also contain a memo field which holds supplementary information, accessible only be the recipient.
Ethereum and Zcash
Now that you know what Zk-Snarks is, it’s also worth mentioning Ethereum plans to integrate Zk-Snarks in its Metropolis phase. They plan an alliance with Zcash that will include a mutual exchange of value.
Zooko Wilcox, chief developer of Zcash, explained the future of such an alliance during Devcon2 in Shanghai. He said there are three ways Zcash and Zk-Snarks could be integrated with Ethereum.
The first method is known as Baby Zoe (Zoe stands for Zcash on Ethereum). It adds a Zk-Snark pre-compiler and creates a mini Zcash smart contract on the Ethereum network. This method explores the possibility of creating a Zk-Snark dApp on top of Ethereum’s blockchain.
The second method is to integrate Ethereum’s computability into Zcash’s blockchain. Wilcox pointed out that Ethereum’s greatest asset is its computability and the possibility of integrating a Zk-Snark based blockchain into it is something that should be investigated.
Project Alchemy is the third possibility and also the one with the highest potential. The method would allow the two blockchains to connect and interoperate. To do this, Zcash plans to clone the BTC Relay, an Ethereum script that was developed to create a Bitcoin light client inside Ethereum. The same concept will be applied to create a Zcash light client inside Ethereum.
Assuming this method will work, it may very well bring us the first decentralized currency system in the world that supports the development of dApps with zero knowledge included in it.
The future of Zcash
Zcash is a promising cryptocurrency that’s highly appreciated by those familiar with the crypto industry. Even during this year’s bear market, the coin retained a steady value with the occasional spike.
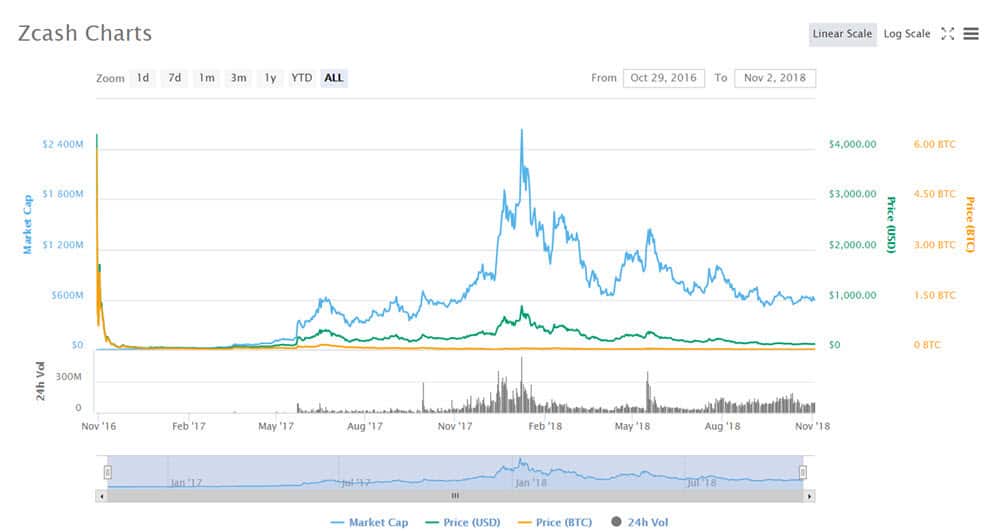
Right now, Zcash has a market cap of $601,776,608 and the value of 1 ZEC is $116.90.
It is quite obvious why Zcash is so valued as the privacy it provides is essential not just to individuals but also for large enterprises.